First, preface: Xiaomi launched a new whole house routing Mesh networking scheme to solve the pain point of signal dead angle.
With the popularity of WiFi 6, more and more families have upgraded their routes just to enjoy the extremely fast networking experience.
However, based on the characteristic that the higher the speed in the 5GHz band, the worse the wall penetration. If the home is loaded with walls, ceilings or floors, the signal loss will be obviously attenuated. For example, if you change rooms, the mobile phone is playing games or brushing videos, there will be obvious jams and disconnections. At this time, you have to use 2.4GHz to connect.
However, 2.4GHz is now in a relatively saturated state, and it has also become the hardest hit area. Bluetooth mouse, Bluetooth headset, smart home, microwave oven and other devices may cause channel congestion.Under such circumstances, the stability performance of 2.4GHz is even worse than that of traffic surfing, and the experience is very worrying.
In fact, in order to achieve the effect of whole house coverage, it is only necessary to build a Mesh network, which is also the most popular whole house coverage scheme at present.
The Xiaomi whole house wireless router received by Fast Technology is the protagonist we want to test.

Mesh, as a complete set of distributed network solutions, is also a solution with low barriers for users to get started. Its advantages are very clear: simple networking, seamless roaming handover, and free addition of sub-routes to realize regional wireless enhancement.
Xiaomi whole house routing supports self-developed Mesh technology, which can be networked by wired, wireless and mixed methods, and can also form a unified whole house network with many Xiaomi /Redmi routers.
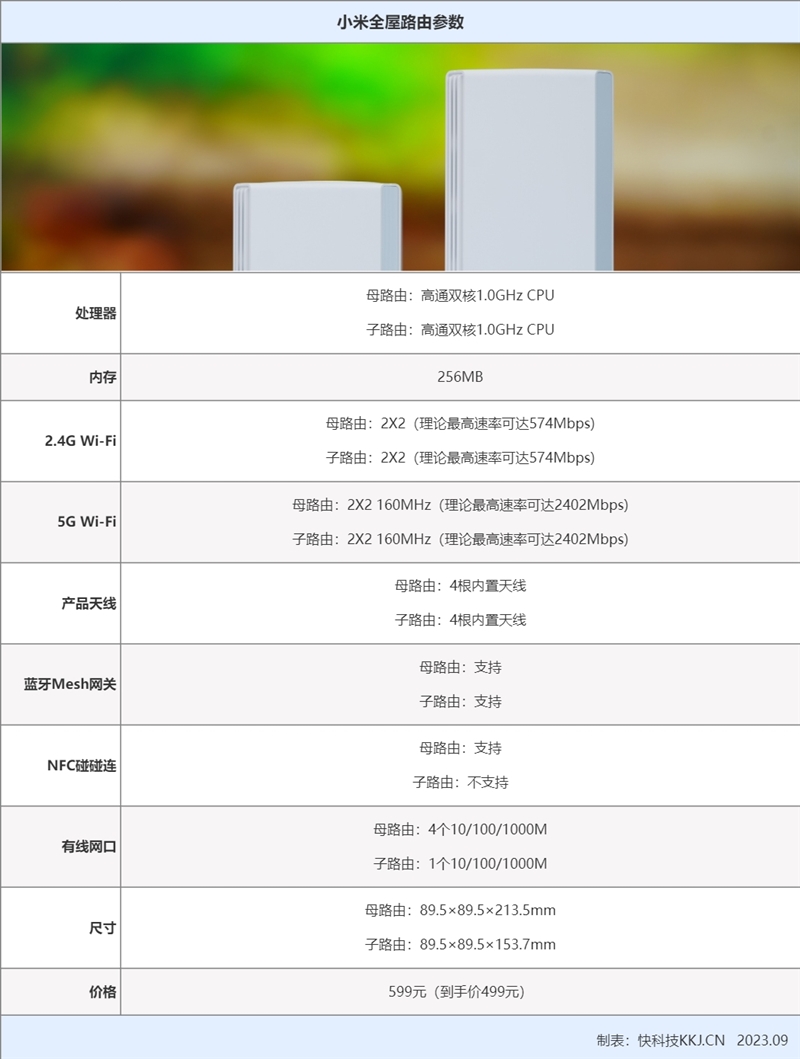
In terms of specifications, this router supports WiFi 6 technology, and provides a total of 5 Gigabit wired network ports (4 mother routes and 1 child route), while wireless supports a large bandwidth of 160Hz, with 4 independent antennas, and the maximum theoretical wireless rate of 2.4GHz and 5GHz dual-frequency concurrency is 2976Mbps.
The positioning of Xiaomi’s whole house routing is an entry-level WiFi 6 router. This configuration can be said to be full of sincerity.
Next, let’s take a look at the performance of this Xiaomi whole house route in terms of signal, coverage and experience.
Second, the appearance: pure white appearance, fashion and simplicity, and all the mother and son routes have built-in four antennas.

Xiaomi’s whole house routing adopts mother-child design, all of which are pure white+square shape, which continues Xiaomi’s simple but not simple design as always.
The bus route with a slightly larger size is 89.5 × 89.5 × 213.5 mm; The child routing size is 89.5×89.5×153.7, which is slightly smaller.
This sub-and-bus route has built-in four antennas, which all use 1GHz CPU and 256MB memory, and all support 2×2 2.4GHz Wi-Fi and 2×2 160MHz 5GHz Wi-Fi.
After being powered on, the 1 mother and 1 child can automatically network in 0 steps, which greatly reduces the trouble for users to manually change the configuration.


The above picture shows the sign of NFC on the top of the parent route, but unfortunately the child router (below) is not equipped with NFC function.
Guests at home need to connect to WiFi, and they can connect to the Internet through NFC at the touch of a supported mobile phone. Even if you forget your password, you don’t have to worry, which saves the trouble of asking.

Xiaomi Mesh WiFi6 is printed on the bottom, indicating that Xiaomi’s self-developed Mesh intelligent connectivity function is supported, and multiple networks can be established by wired, wireless and mixed methods.
Even for complex apartment types, only one parent route is needed to connect 9 sets of routes, and it is easy to set up a whole-house network to achieve whole-house coverage.

A list of interfaces of the parent route, including Mesh (short press)/Reset (long press) button, four adaptive WAN/LAN ports with 1Gbps rate, and power interface.
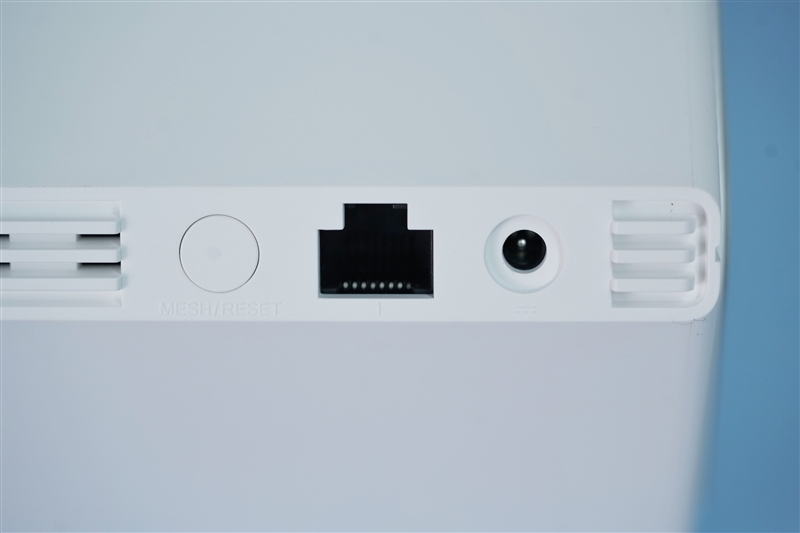
The interfaces of sub-routes are relatively simple, including Mesh (short press)/Reset (long press) button, a 1Gbps WAN/LAN adaptive network port and power interface.
The network port can be connected to the parent routing network port or lower-level computer equipment, which is convenient for users to expand the use scenarios of different rooms.

Charging port, instruction manual and network cable of the sub-bus route attached in the package.
3. Mesh networking and speed transmission test: In the 5G band, there is also 316Mbps at the far end of the whole house without inductive switching.
Xiaomi’s whole house routing supports 3000M wireless rate, that is, from 2.4G band with 574Mbps rate and 5G band with 2.4Gbps rate, reaching a total rate of 2976Mbps.
Moreover, one parent route and one child route are respectively equipped with four external signal amplifiers, that is, a total of eight external signal amplifiers.
The maximum number of connections can support 256 WiFi devices and 200 Bluetooth devices, which is more than enough for ordinary houses.
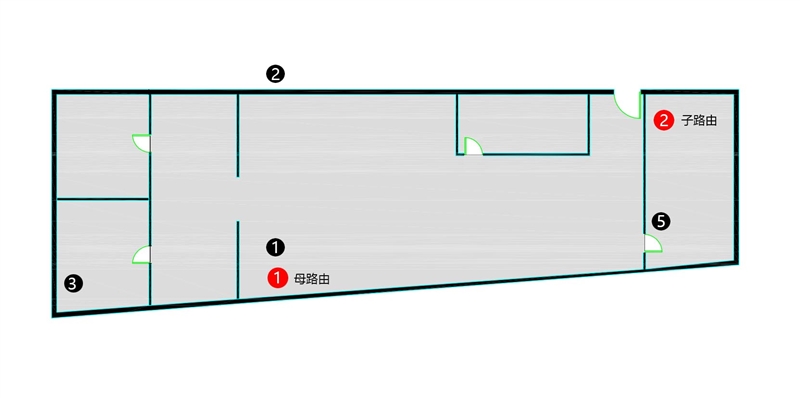
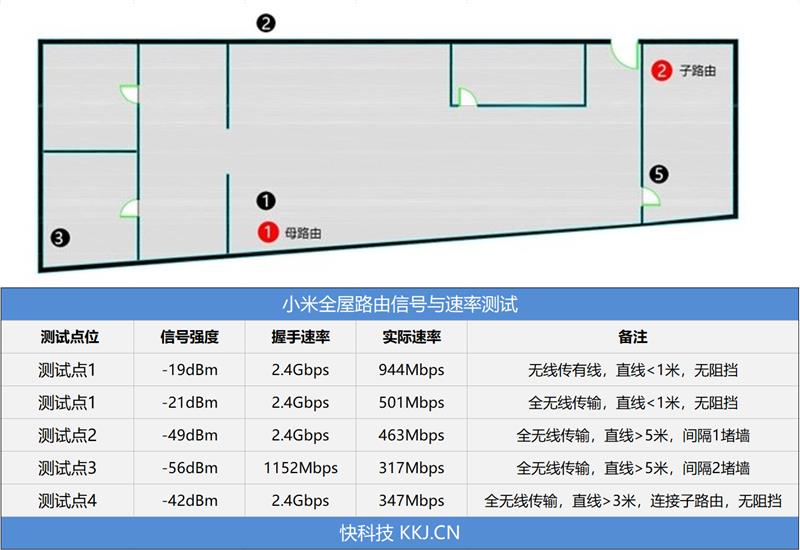
The environment we tested is an office, with an area of about 300~400 square meters, which is at least twice as large as the conventional residential environment.
The red dot is the installation position of the parent-child route, and the distance between them is about 8 meters, and the black dot is the test position.
Let’s take a look at the performance of Xiaomi’s whole house wireless routing.
1. Roaming test
Xiaomi wireless routing supports Mesh networking, which is very simple to get started. Just enter the gateway address of the parent route and manually complete the routing configuration, and it can automatically complete Mesh networking.
This process is very insensitive, and it can be easily completed if you want to network in different ways, such as wired, wireless and mixed.
If it only covers the whole house, it is suggested that the location of the parent route should be fixed first, and then the child route should be placed in the dead corner of the signal after the networking mode is set, thus completing the network coverage of the whole house.
Moreover, the bus route can be connected with up to 9 sets of routes, and even if there are more walls and more complicated apartment types, it can achieve a smooth connection experience without dead ends.
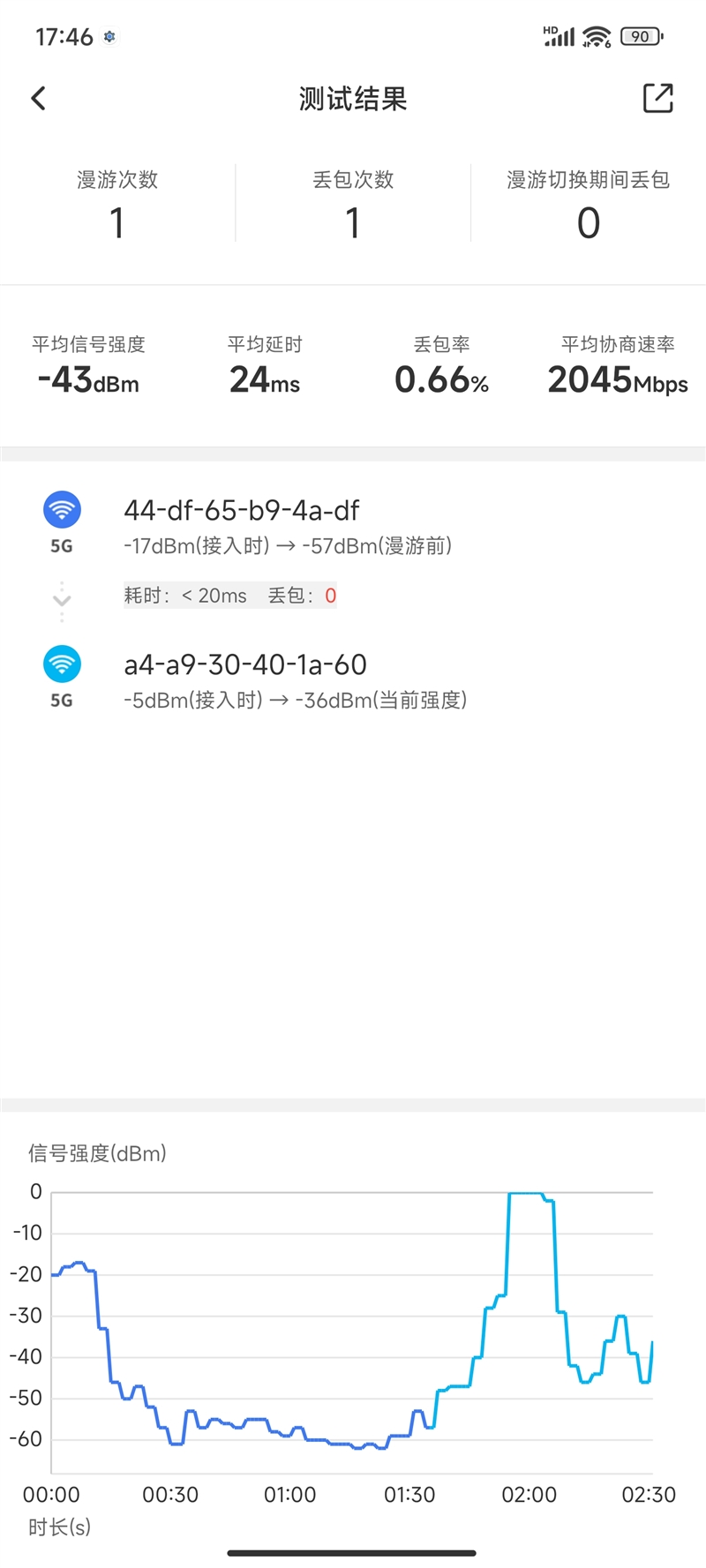
We also tested the signal strength of roaming and walked around the office randomly.
The signal strength of the slave route reached 57dB before the automatic switching roaming.
After automatic switching to the sub-route, the signal strength is further reduced to 36dBm, and the average delay is about 24 ms.
This process is basically non-inductive, avoiding the problem of attenuation of 5GHz WiFi+WiFi 6, and making the whole house available.
If there are high requirements for signal strength and transmission speed, more sub-routes can be set, which can make the signals in all rooms basically reach a very good level.
— — transmission speed
Xiaomi Wireless Routing makes the antenna into a built-in antenna, so what about its signal, intensity and transmission rate in different environments? Let’s directly measure its performance.
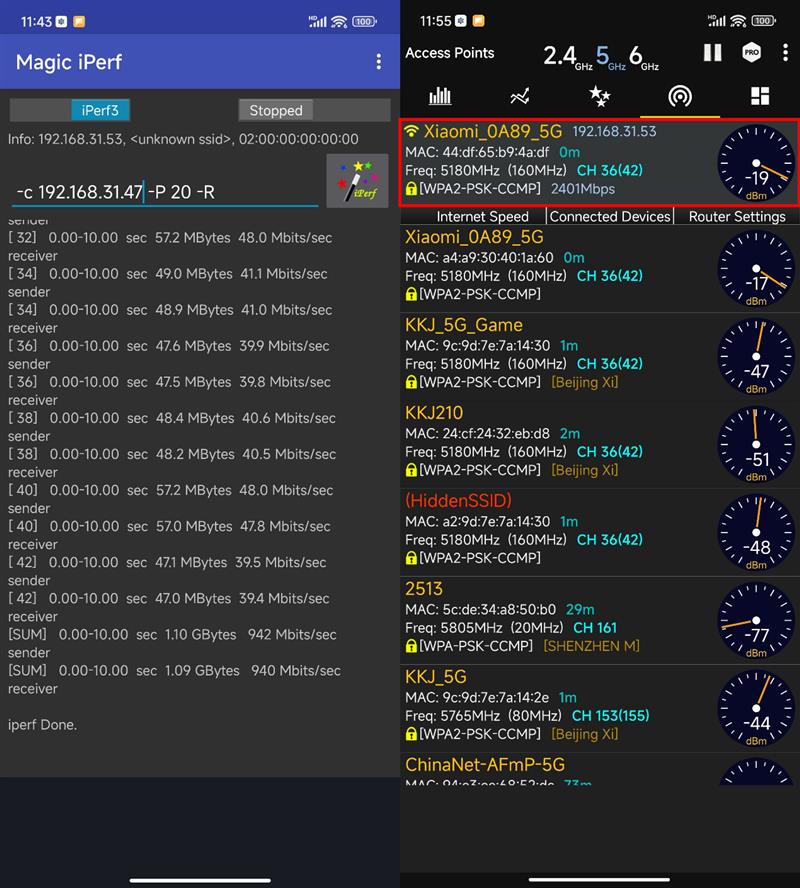
The PC used for testing is also in the test point 1 position with the parent route.
At this time, the PC device is in a wired 1000Mbps link, the wireless rate of the mobile phone is 2.4Gbps, and the signal strength is -19dBm.
In 10 seconds, 1.1GB of data was transmitted to the PC, and the highest speed reached 944Mbps, which can be regarded as gigabit full of blood.
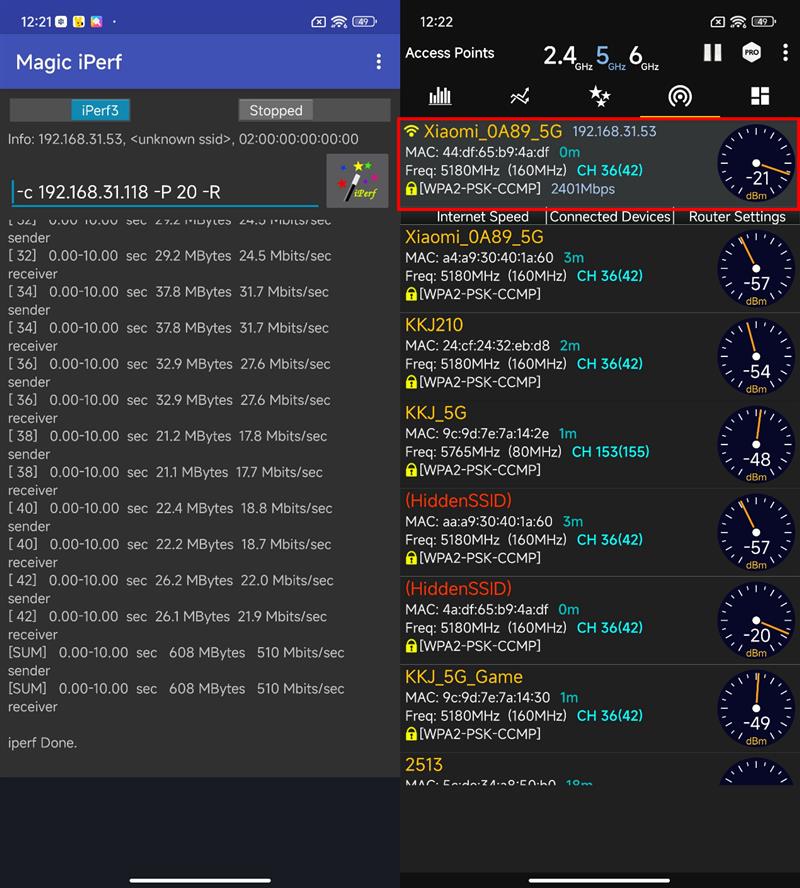
When both PC and mobile phone are wireless, at test point 1, the handshake rate of PC is 2.4Gbps, that of mobile phone is 2.4Gbps, and the signal strength is -21dBm.
In the pure wireless environment, it is very easy to be disturbed by the environment, but the mobile phone transmits 608MB of data to the PC within 10 seconds, and the speed is about 510Mb/s, which is still very ideal.
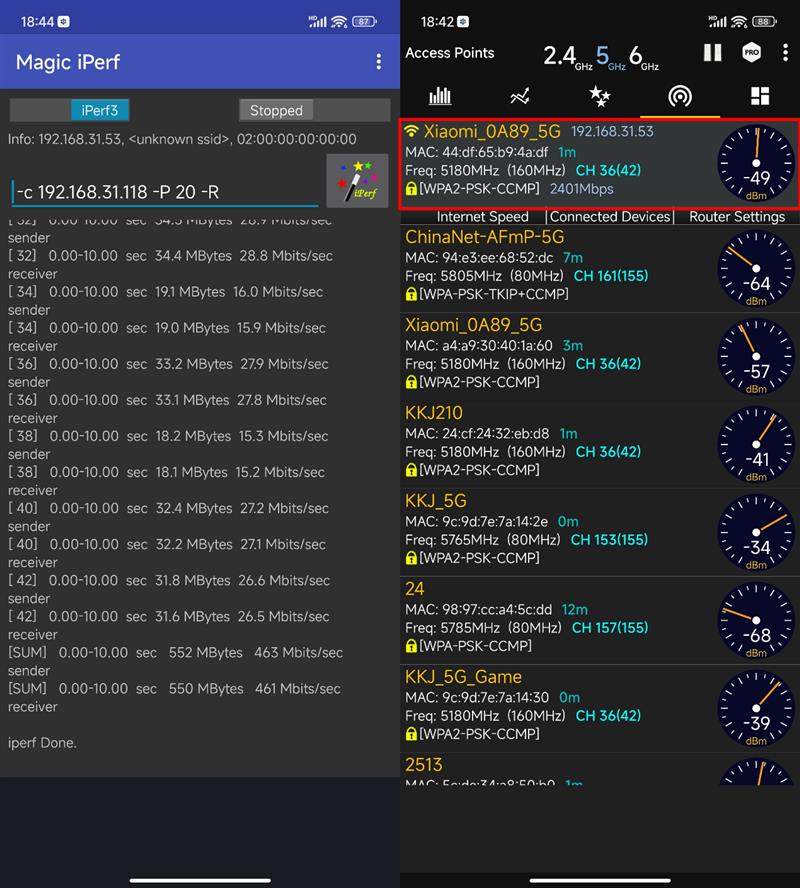
At this point, we separated a wall at test point 2, the handshake rate was 2.4Gbps, and the signal strength was obviously blocked, reaching -49dBm.
Within 10 seconds, the mobile phone transmitted 552MB of data to the PC, and the maximum speed was about 463Mbps, so the loss was not too obvious.

At test point 3, the handshake rate of the mobile phone dropped to 1152Mbps, and the signal strength was -56dBm.
Within 10 seconds, the mobile phone transmitted the maximum data of 377MB to the PC, and the maximum speed was about 316Mbps.
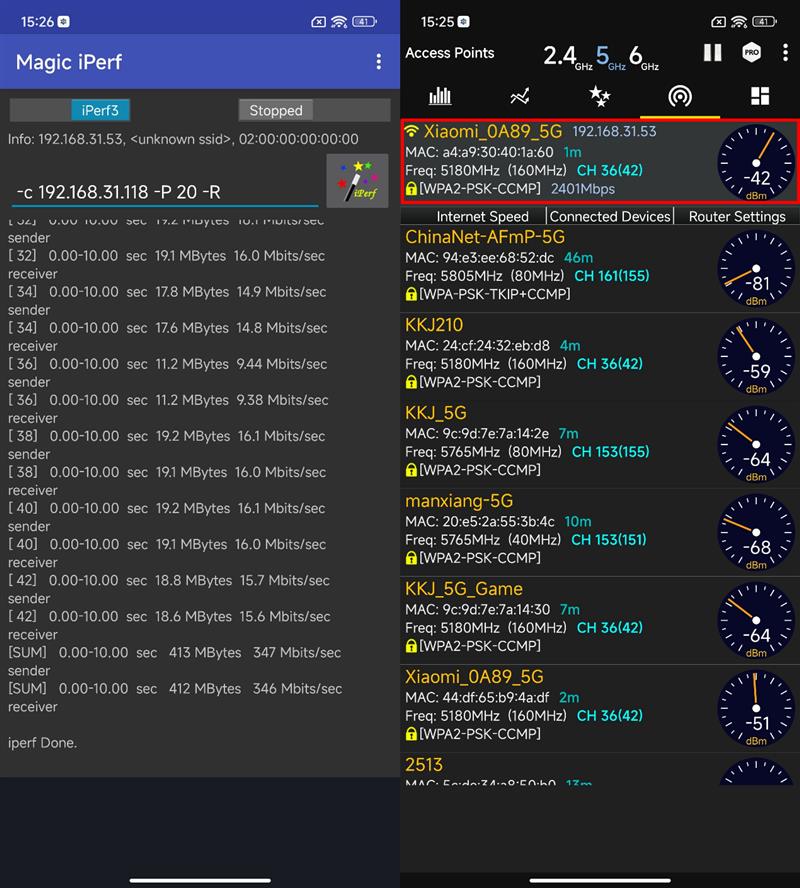
At test point 4, the child route is connected at this position, but the distance from the parent route is long, at least about 10 meters.
Handshaking rate of mobile phone is 2.4Gbps, and signal strength is -42dBm.
Within 10 seconds, the mobile phone transmitted the maximum data of 412MB to the PC, and the maximum speed was about 347Mbps.
The following figure is a summary of the table:
Fourth, summary: only 499 yuan can cover the best choice of the same price in the whole house.
1. Entry level also has excellent experience. Mesh realizes 5G+WiFi 6 coverage of the whole house.
This whole house wireless routing brought by Xiaomi, although it focuses on entry-level Mesh routing, has achieved the best existence in the same price range while focusing on affordable prices.
We actually measured this route. Although the antenna is built in, the coverage rate is not compromised. In a room of 300~400㎡, the basic coverage can be achieved by only one parent route and one child route. The wall-crossing experience is also excellent, and the signal strength is also very ideal.
If you encounter a residential environment with a slightly larger area and more walls, it is recommended to put a sub-route in one room conditionally, so that the whole house can enjoy the carefree experience brought by 5GHz WiFi+WiFi 6 and bid farewell to the signal dead angle completely.
Thanks to the characteristics of wireless roaming, you can play games and watch videos in any room, without worrying about dropped calls and jams caused by node switching.
2. The small functions of secret-free network access and secret-changing synchronization are very worry-free, which adds extra points to Mijia ecology.
With more and more ecological products of Xiaomi, this router also has unique functions that are different from other routers.
For example, smart devices that are not connected to the network are exempt from encryption, and all smart homes are directly synchronized.Although it looks unremarkable, if you encounter a lot of smart homes, you have to reconnect after changing the hot password. I believe this workload is very headache.
Although these functions are insensitive, they can’t be without them, which makes users worry enough about their daily use and adds a lot of points to the ecological experience of Mijia.
There are also these features of NFC, which can connect with friends and relatives at home, and you can connect to the internet with a touch of your mobile phone, avoiding the embarrassment of remembering your password.
It can be said that Xiaomi has achieved the experience of "no one has me, and people have me" in these small functions.
3, the most competitive price of the same kind is only 499 yuan.
The most eye-catching thing is its price.Some e-commerce companies have killed the starting price to around 499 yuan.We must know that the cheapest e-commerce can buy in the market is around 599 yuan. Xiaomi once again shows the true nature of "price butcher" and gives full play to its very strong competitiveness.
If you want to experience the carefree experience of full-house coverage without dead ends, or have a headache about large-sized network coverage and don’t know how to choose, and the budget is not high, then I think this millet full-house routing is your best choice.